Did you know that Windows Server 2012 comes with the BPA already installed? In the past, it was necessary to acquire every BPA by downloading
- What Are The Best Mill Cards Edh Mill Cards?: Edh The State Of Mill In Commander
- What Is The Best Way To Avoid Running Aground, How To Avoid Running Aground
- 2023 Best Steakhouses San Antonio Best Steak In San Antonio, The Best Steakhouses In San Antonio
- Scooby_Dood’S Neopets Best Battledome Items ? Neopets Neopets Best Cheap Battledome Items
- Best Prom Looks 2016 – 3 Best Prom Looks For 2016
http://www.microsoft.com/en-us/download/details.aspx?id=15556
Bạn đang xem: Run Best Practices Analyzer Server 2012 R2 Best Practices Analyzer #Bpa #Winserv
Now in 2012, the BPA is integrated; this is a fantastic addition, but I’ve noticed that many users and even some IT administrators are unaware of it.
The BPA can be inspected using either PowerShell or a graphical user interface.
Version for the GUI:
You should check the status of your local server in the service manager (this is my demo server, so there should be lots of mistakes).
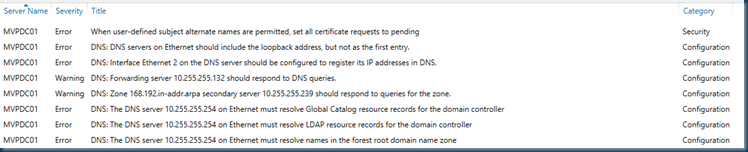
Select Assignment, then choose the BPA test. and it will produce a neat list of configuration items as output.
However, I should add that you can even further customize your experience with powershell.
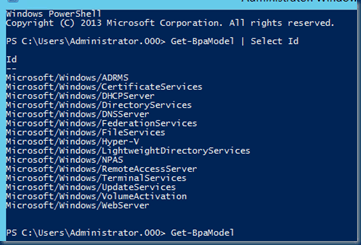
Determine whether or not any relevant BPA models are currently accessible.
Xem thêm : Picture Frame Ideas For Best Friend, Best Friend Picture Frames For Sale
Find-BpaModel | Pick Id
Id — Microsoft/Windows/ADRMS Microsoft/Windows/CertificateServices Microsoft/Windows/DHCPServer Microsoft/Windows/DirectoryServices Microsoft/Windows/DNSServer Microsoft/Windows/FederationServices Microsoft/Windows/FileServices Microsoft/Windows/Hyper-V Microsoft/Windows/LightweightDirectoryServices Microsoft/Windows/NPAS Microsoft/Windows/RemoteAccessServer Microsoft/Windows/TerminalServices Microsoft/Windows/UpdateServices Microsoft/Windows/VolumeActivation Microsoft/Windows/WebServer
Some scans are quick while others take a little longer, but all of these models can be run easily and quickly on your server’s built-in infrastructure.
A Microsoft/Windows/WebServer with the Invoke-BpaModel
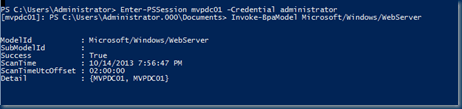
Check out a breakdown of the BPA data according to Impact here.
Get-BpaResult Group Severity | Microsoft/Windows/DNSServer
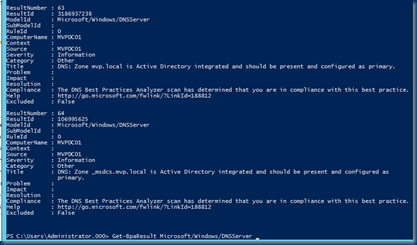
All the contents of the console will be displayed in a list.
Check out the full report for everything rated as “Warning”:
Microsoft Windows DNS Server Get-BpaResult |? Threat Level = “Warning”
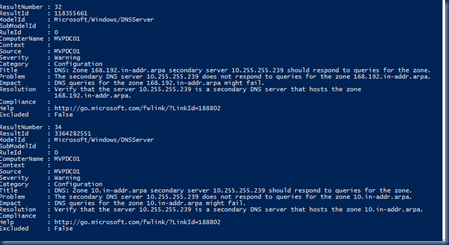
Xem thêm : Best Fitness Tonawanda Hours, Gyms With Group Fitness Classes In Tonawanda, Ny
Moreover, if you wish to omit specific things,
Modify-BPAResult -Id Unique Model Number Leave out if $true
Start with these examples, but know that there are many more avenues open to you.
If you know all the Command lets, then yes, it’s simple.
Look here:The Junk E-Mail Filter in Outlook 2003 Has Been Improved, So Should You.
It’s not difficult to get going
I’d like to get the command for the bpa.
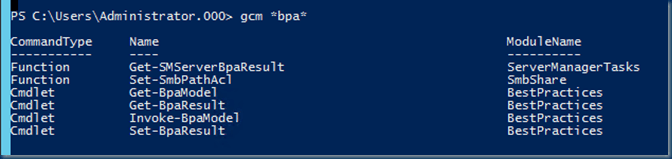
This completes the set of available BPA commands.
Guidelines for the Get-BpaModel command Options for the Get-BpaResult Command Standards for the Invoke-BpaModel Command Procedures for Executing the Set-BpaResult Command
Nguồn: https://directmarketingcenter.net
Danh mục: Best









